Salesforce Connected App Security
Sept 2025 Changes and Best Practices
Salesforce recently announced some sweeping changes to the utilization of Connected Apps. Beginning early September, access to uninstalled Connected Apps will be limited to users who have a new, dedicated permission assigned — “Approve Uninstalled Connected Apps”. This change is part of Salesforce’s security hardening to prevent social engineering attacks where bad actors trick users into connecting their org to malicious apps (for example, unauthentic versions of tools like Data Loader). Let’s review what this means, what actions you’ll need to take, and take a step back and talk about Connected App security overall.
What Are Uninstalled Connected Apps?
So, what exactly are uninstalled Connected Apps, and how do you know if anyone in your org is utilizing one? There are plenty of practical uses for an uninstalled Connected App. These are third-party applications that you are authorizing (via OAuth) to interact with your Salesforce data in some manner. Maybe your organization uses Power BI to query data from Salesforce for outside analysis. Or perhaps you are a nonprofit utilizing Donorbox for donation management, which feeds donor and donation data into your org. In either case, these apps do not have to be installed in your org for the functionality to operate. With this upcoming change, if the running users for each of these integrations do not have the “Approve Uninstalled Connected Apps” permission assigned, the functionality will break.
How to Identify Your Uninstalled Connected Apps
There are two ways to assess your utilization of uninstalled Connected Apps.
Method 1: Using the Salesforce UI
The first is to navigate to Setup → Connected Apps OAuth Usage, and you’ll see a list of all the utilized Connected Apps in your org, like in this example screenshot below.
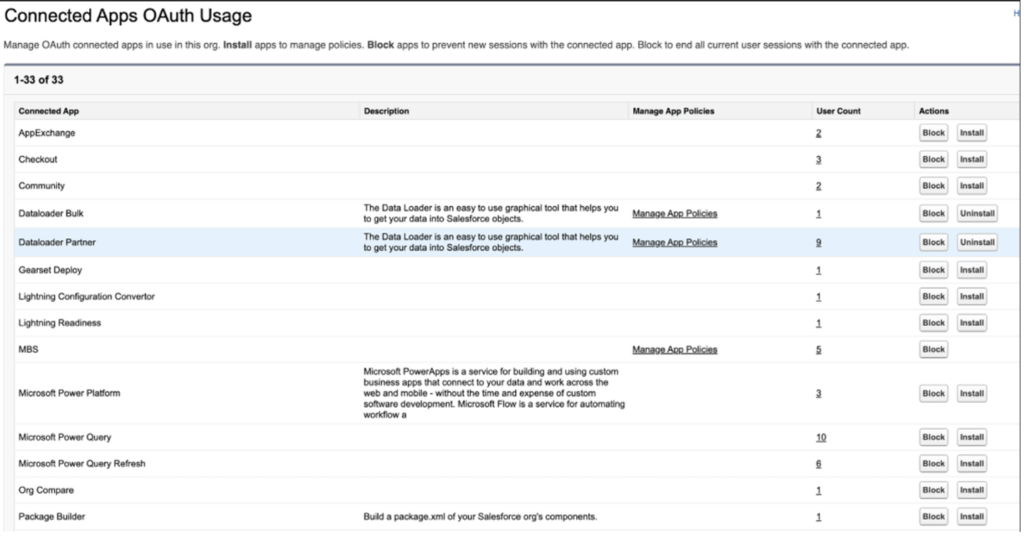
If you see an “Install” button in the “Actions” column for a given app, that means the app is uninstalled. For each uninstalled app, you’ll need to click into the hyperlinked number in the “User Count” column to be taken to a screen listing the usernames of each of the users who have utilized the app, the most recent time they’ve used it, as well as the number of times they have used it.
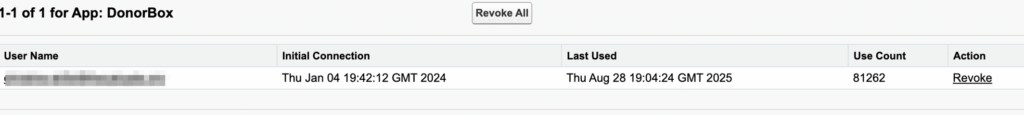
I’m not the biggest fan of this method for immediate assessment, because the Connected Apps OAuth Usage page includes all Connected App use in the history of your org. Meaning you could have dozens of apps listed to click through – including those that haven’t been utilized for years. Attempting to step through all of those could be quite tedious and time-consuming.
Method 2: SOQL Query for Efficient Assessment
If you’re comfortable with SOQL – either via the Developer Console or Data Loader — here’s a SOQL query that will return a list that will be much more efficient to assess:
SELECT Id, AppName, UserId, User.UserName, CreatedDate, LastUsedDate, UseCount, AppMenuItemId
FROM OAuthToken
WHERE CreatedDate = THIS_YEAR AND AppMenuItemId = NULL
ORDER BY CreatedDate DESCThis will return you a list of each user/app combination of all uninstalled Connected Apps for the current year. If you wish to see a more thorough list of all Connected App utilization, simply remove the “AppMenuItemId = NULL” “WHERE” clause. Note, if you’re running this as an export via Data Loader, you’ll need to set the “Show All Salesforce Objects” setting.
Next Steps: Assigning the New Permission
The “Approve Uninstalled Connected App” permission should now be available in all Salesforce orgs as of this week. If you’re not seeing it, please reach out to your Account Executive. So, once you’ve identified the utilization here, you can quickly ensure all your valid usage of these continues to function as expected. Given the very abrupt rollout, Salesforce has not yet announced an official date when the standard permission change will go into effect. The language is currently “early September”, so we should expect it to be in the next week and a half or so.
The Limitation: An All-or-Nothing Approach
While it’s critical to assign this new permission to ensure your integrations do not break, it’s also an oversimplified solution that doesn’t quite absolve you from ensuring your users aren’t falling victim to bad actors. It’s an all-or-nothing permission, meaning, the users you assign this to have access to utilize any uninstalled Connected App. So, if your running user for a critical integration encounters a well-designed social engineering attempt (and let’s face it – they’re getting harder to detect), there’s nothing stopping them from inadvertently granting a malicious application access to your Salesforce data.
A More Comprehensive Solution: API Access Control
To more comprehensively address this solution, Salesforce has also recently rolled out a new feature, API Access Control. With this feature, you can configure policies for which users (or groups of users) are allowed to utilize which specific Connected Apps. It also outright prevents the utilization of any uninstalled Connected Apps, period. So, this means that your Salesforce Admins or Consulting Partners will need to take a few more steps for each new app your organization wishes to utilize; however, you can take peace of mind in knowing that your org is that much more secure. Another important thing to note is that this feature is only available by request, so you’ll need to reach out to your Account Executive to enable it.
Get Expert Help with Your Salesforce Security
Looking for assistance in the assessment of your Connected Apps, configuration of API Access Control, or just want to chat more about security? Our experienced Salesforce consulting team is here to help you navigate these critical security changes. Contact us today to discuss your specific situation and develop a customized action plan that keeps your Salesforce data secure while maintaining the integrations your business depends on.